Avinode OAuth 2.0 Token Management
Avinode supports OAuth 2.0 Client Credentials Grant for short-lived access tokens used to authenticate API requests.
Prerequisites
OAuth feature enabled for your company account. Contact [email protected] if not active.
For OAuth token management, a user account in Avinode will require the following permissions:
- Company APIs, and,
- Technical Staff
Retrieve OAuth Credentials
- Log in to your Avinode Marketplace account (https://marketplace.avinode.com/) with valid user credentials.
- Navigate to Company -> APIs -> [Your Connection].
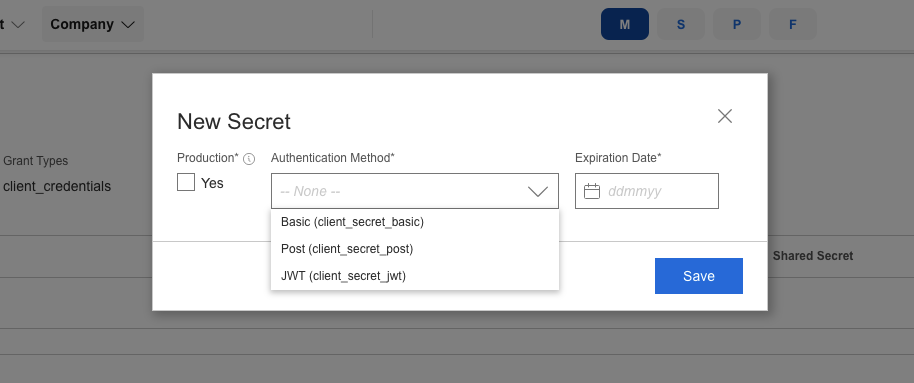
- Under OAuth, copy the Client ID and generate a Client Secret by clicking the button New Secret.
-
Choose authentication method (
client_secret_basic,client_secret_post, orclient_secret_jwt).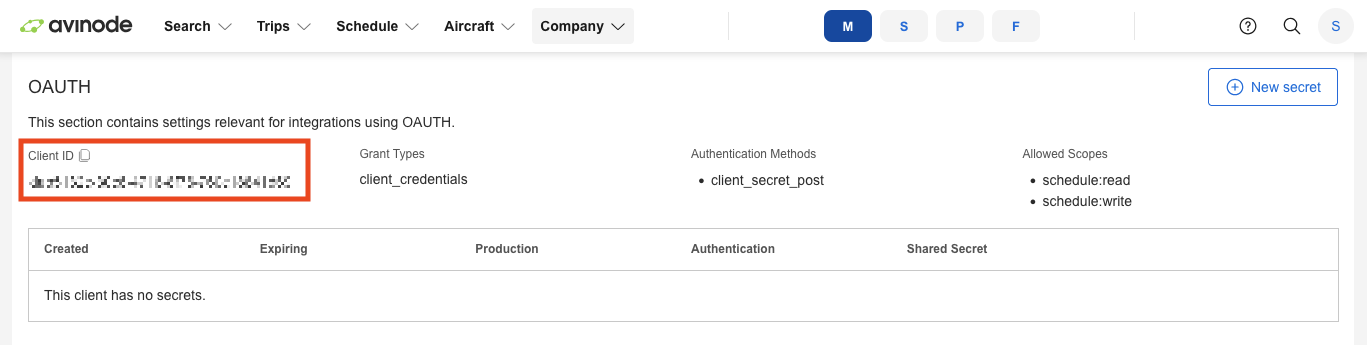
-
Select an expiry period for the secret.
⚠️ Please note: Store credentials securely — the secret is only displayed once
-
Request an Access Token
Endpoint
Headers
Accept: application/json
Content-Type: application/x-www-form-urlencodedBody parameters
| Parameter | Description | Required |
|---|---|---|
grant_type | Must be client_credentials | Yes |
client_id | Your OAuth Client ID | Yes |
client_secret | Your OAuth Client Secret | Yes |
expiresInMinutes | Optional. Token lifetime (1–120 min, default 30 min if not included). | No |
Example Request
curl -X POST "https://sandbox.avinode.com/api/oauth/token" \
-H "Accept: application/json" \
-H "Content-Type: application/x-www-form-urlencoded" \
-d "grant_type=client_credentials" \
-d "client_id=YOUR_CLIENT_ID" \
-d "client_secret=YOUR_CLIENT_SECRET" \
-d "expiresInMinutes=30"Example Response
{
"access_token": "$0m3_eX@mp1e_0f+TOk3n...",
"expires_in": 1799,
"token_type": "Bearer"
}Using the Access Token
Include the token in your Authorization header
Authorization: Bearer <access_token>Tokens expire automatically after their expires_in duration. When expired, request a new one. Refresh tokens are not issued for this flow.
OAuth Workflow diagram
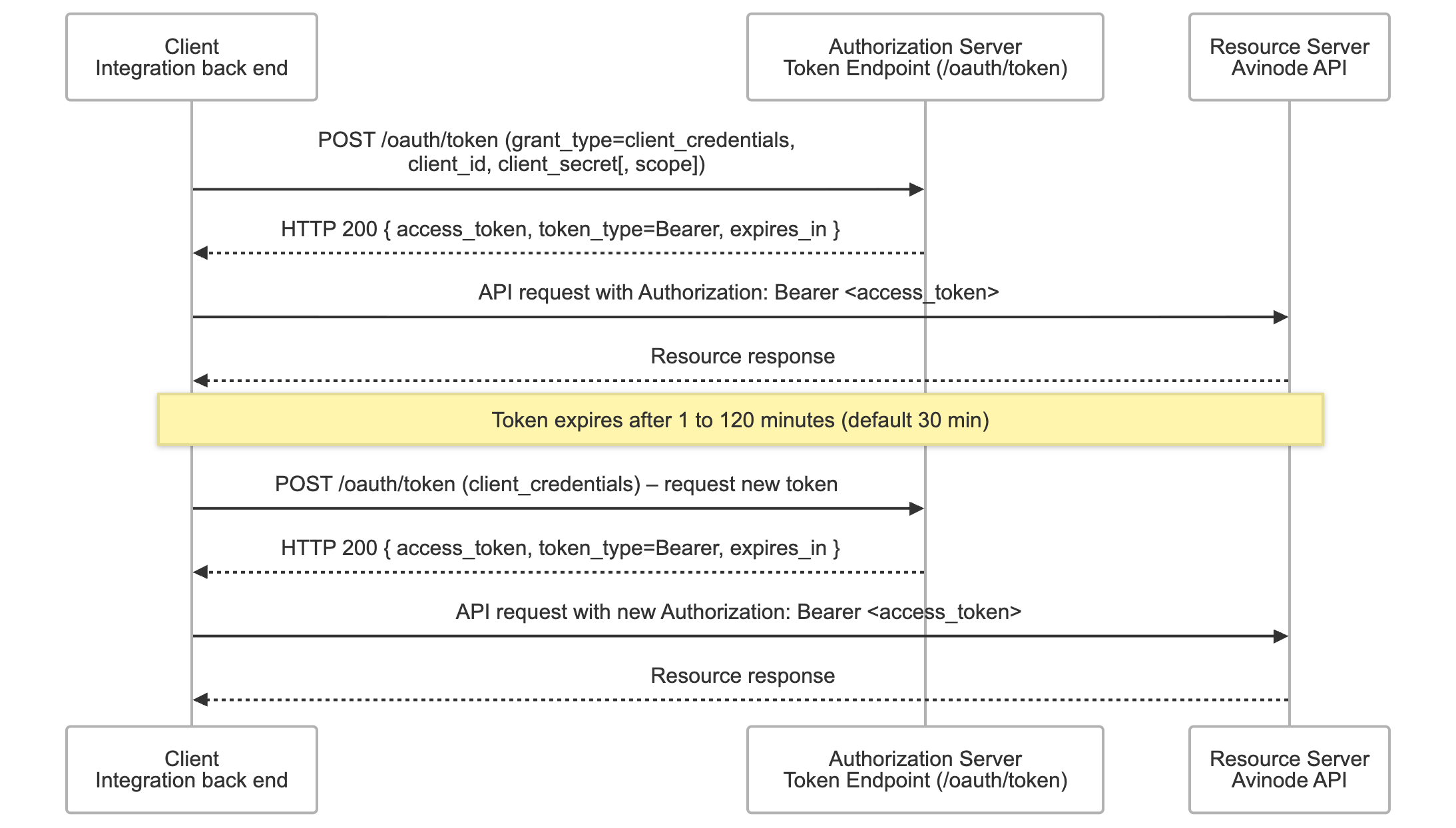
When using OAuth to authenticate against the Avinode APIs, the Avinode Authorization Server issues a short-lived Access Token.
This token represents the client’s authorisation to access Avinode’s protected API resources and is obtained by making a request to the OAuth Token Endpoint (POST /api/oauth/token) using the Client Credentials grant type.
Once issued, the Access Token is used in all subsequent API calls as a Bearer token inside the HTTP Authorization header.
Troubleshooting
Below are some common errors developers may encounter when requesting or using OAuth Access Tokens.
| HTTP Status | OAuth Error Code | Description | Resolution |
|---|---|---|---|
| 400 | — | Missing or incorrect Content-Type header. | Add Content-Type: application/x-www-form-urlencoded. |
| 401 | invalid_client | Provided client credentials invalid. | Verify client_id / client_secret and authentication method. |
| 401 | unauthorized_client | Grant type not allowed. | Ensure OAuth is enabled for your company. |
| 401 | invalid_token | Token expired or malformed. | Request a new token. |
| 429 | — | Too many requests. | Cache and reuse tokens during validity. |
| 500 | — | Internal error. | Retry after delay; if persistent, contact support with timestamp and payload. |
Additional Implementation tips
- Use HTTPS exclusively – All requests to Avinode OAuth endpoints must use HTTPS. Requests made over HTTP will be rejected for security reasons. Verify your integration does not downgrade via load balancers or proxies.
- Default token lifespan – If you omit the
expiresInMinutesparameter, the system defaults to 30 minutes. The valid range is 1 to 120 minutes. - No refresh tokens in this flow – The Avinode OAuth implementation uses the Client Credentials grant, which does not issue refresh tokens. When a token expires, simply request a new one using the same
client_idandclient_secret. - Revoke tokens when needed – You can revoke an active access token at any time under:
Company -> APIs -> [Your API Connection] -> OAuth. Revoking a token immediately invalidates it and forces a new authorization cycle, which is recommended if you suspect a key has been exposed. - Rotate credentials regularly – To maintain security, rotate your
client_secretperiodically (for example, every 90 days) and remove unused OAuth connections. - Cache tokens intelligently – To avoid
HTTP 429 – Too Many Requestserrors, store and reuse each valid access token until it expires. Re-authenticate only when necessary. - Validate timestamps and time zones – Ensure your system clock is synchronized and you use solely UTC. OAuth expiration checks depend on accurate UTC time.
- Error context for support – When contacting support, include the timestamp, payload, and response body from the failed request. This allows quicker troubleshooting and log correlation.
Updated 3 months ago